While it might be the biggest cybersecurity event of the year, RSA 2018 can be overwhelming. The crowds, lectures, sparkly gadgets, and more can confuse the senses and make you forget about your top security priorities. Don’t worry, The Media Trust is there to answer your questions about digital security and compliance. No matter what your industry (banking, ecommerce, media, government, hospitality, etc.), your corporate mobile apps and websites have the potential to be your greatest business assets or largest source of security, revenue, and reputational risks. Learn how we close the gaps in your security and compliance posture that traditional web appsec tools don’t.
Here are five reasons to swing by our booth next week:
- Identify and Remedy your Digital Shadow IT
Many industry experts will caution you against shadow IT, only a handful will tell you where to look for it. We not only expose the shadow IT on your enterprise mobile apps and websites but also detect concealed threats like malicious code injection, unauthorized data collection, latency issues, as well as help remediate these issues via our Digital Vendor Risk Management platform.
2. GDPR Compliance – we walk the talk
Your mobile apps and websites are out of control – no, this isn’t a hyperbolic statement. With third parties contributing anywhere between 50-75% (sometimes as high as 95%) of your code base, controlling data collection activity that violates the GDPR directive isn’t straightforward. Speak to us about how to regain control of your digital assets.
Catch our session, GDPR Compliance–You forgot your digital environment, on Thursday, April 19, between 1:45 pm – 2:30 pm at Moscone West 2018. Session ID: GRC-R12.
3. Attack intel (not the just threat intel)
Our Malware Attack Data enables you to block active attacks targeting your endpoints through frequently whitelisted, premium websites – news, travel, social networks, and more. Let’s talk about how our attack data can augment your AVs, firewalls, web filters, and blocking solutions.
4. Free website audits
Want a sneak peek into your mobile app and website shadow IT? Get a free website audit and discover the surprising number of domains and cookies (including user identifying cookies) operating outside the perimeter of your IT and security tools
5. Coffee, martinis, and comfy couches
If you don’t want to talk security and compliance, and are just curious about The Media Trust or are badly in need of caffeine, drop by and say hi! Here are our Coffee and Martini Bar hours –
Coffee Bar: 10:00 am – 1:00 pm, April 17-18, 2018
Martini Bar: 4:00 pm – 6:00 pm, April 18, 2018
We’ll be there at Booth #2507, South Hall, Moscone Convention Center, San Francisco. Enter the South Hall, turn right, and follow the inquisitive masses.





 Yes, parked domains are a security problem. Let’s take the real-world example of pantry moths as an analogy. Imagine hoarding supplies in your kitchen pantry due to forecasts like h
Yes, parked domains are a security problem. Let’s take the real-world example of pantry moths as an analogy. Imagine hoarding supplies in your kitchen pantry due to forecasts like h


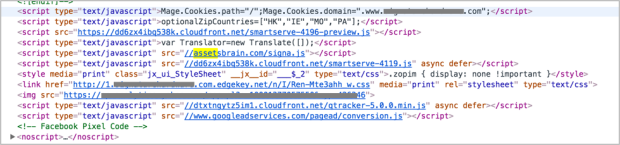 Malicious domain in the website’s footer
Malicious domain in the website’s footer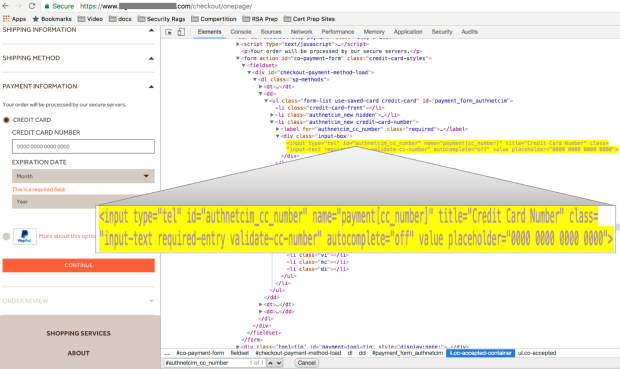 Execution of transparent overlay
Execution of transparent overlay